
Before I changed to OpenVPN I used racoon IPSEC tool. It was very unstable for my setup, because one VPN site has a dynamical IP-Address and only with dirty workarounds was it possible to use it.
After some unsuccessful tries with openswan:( I decided to try OpenVPN and I had luck I found very useful blog of (Sébastien Wains) which was my clue to my working VPN.
I draw a little map of my VPN setup:
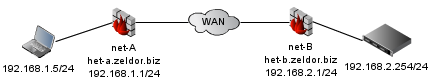
I decide me to use port 8001/UDP for the connection on both sides.
Side-A:
Router/Gateway: 192.168.1.1
WAN-Address: het-a.zeldor.biz
Firewall:
1 2 3 | iptables -A INPUT -i ppp0 -p udp --dport 8001 -j ACCEPT iptables -A INPUT -p ICMP -s 10.0.0.2 -j ACCEPT iptables FORWARD -i tun1 -s 10.0.0.2 -d 192.168.1.0/24 -j ACCEPT |
Enable routing:
1 | echo 1 > /proc/sys/net/ipv4/ip_forward |
Config Side-A:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 | remote het-b.zeldor.biz float port 8001 dev tun ifconfig 10.0.0.1 10.0.0.2 persist-tun persist-local-ip persist-remote-ip comp-lzo ping 15 secret /etc/openvpn/vpn.key route 192.168.2.0 255.255.255.0 chroot /tmp/openvpn user nobody group nogroup log-append /var/log/openvpn/vpn.log verb 1 |
Side-B:
Router/Gateway: 192.168.2.1
WAN-Address: het-b.zeldor.biz
Firewall:
1 2 3 4 5 6 7 | ptables -A INPUT -p udp --dport 8001 -j ACCEPT ptables -A FORWARD -p tcp -s 10.0.0.1 -d 192.168.2.0/24 -j ACCEPT ptables -A FORWARD -p udp -s 10.0.0.1 -d 192.168.2.0/24 -j ACCEPT ptables -A FORWARD -p icmp -s 10.0.0.1 -d 192.168.2.0/24 -j ACCEPT iptables -A FORWARD -p tcp -s 192.168.1.0/24 -d 192.168.2.0/24 -j ACCEPT ptables -A FORWARD -p udp -s 192.168.1.0/24 -d 192.168.2.0/24 -j ACCEPT ptables -A FORWARD -p icmp -s 192.168.1.0/24 -d 192.168.2.0/24 -j ACCEPT |
Config Side-B:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 | remote het-a.zeldor.biz float port 8001 dev tun ifconfig 10.0.0.2 10.0.0.1 persist-tun persist-local-ip persist-remote-ip comp-lzo ping 15 secret /etc/openvpn/vpn.key route 192.168.1.0 255.255.255.0 chroot /tmp/openvpn user nobody group nogroup log-append /var/log/openvpn/vpn.log verb 1 |
Enable routing:
1 | echo 1 > /proc/sys/net/ipv4/ip_forward |
Generate a security key on Side-A and copy it to Side-B:
1 2 | openvpn --genkey --secret /etc/openvpn/vpn.key scp /etc/openvpn/vpn.key root@het-b.zeldor.biz:/etc/openvpn/vpn.key |
Establish VPN connection(execute on both sides):
1 | openvpn --config /etc/openvpn/vpn.conf |
Your remote address could be a IP or hostname or dyndns alias.
Start your VPN at boot:
1 2 3 | vim /etc/default/openvpn # We start our vpn.conf connection (without .conf) AUTOSTART="vpn" |
Test connectivity: (use ping traceroute)
traceroute to 192.168.2.36 (192.168.2.36), 30 hops max, 60 byte packets 1 192.168.1.1 (192.168.1.1) 0.343 ms 0.371 ms 0.431 ms 2 10.0.0.2 (10.0.0.2) 29.157 ms 29.342 ms 29.417 ms 3 192.168.2.36 (192.168.2.36) 30.261 ms 30.626 ms 30.831 ms |

Hi Wil,
generally it’s possible and is very practical to use the same machine for both purposes. Both VPN constructs are very well described here on by blog.
If you have any deeper questions or wish any help, let me know.
Thanks you, i have a question, how can i do the VPN for Remote access and Site To site on The same Server.
Thank you so much !
You really help me :D
Hey David, please take a look into the following post. It’s exactly what you need.
Best Regards
Hi there, in this scenario these are two OPENVPN servers connected together, correct? What else has to be done so I can connect clients to each OPENVPN server?
Thank you
Short and very useful