Q: What is the purpose of the Spanning Tree Protocol (STP)?
A: prevents Layer 2 loops
Q: What creates a loop-free path through a switch network?
A: Spanning Tree Protocol
Q: Which statement is true regarding states of the IEEE 802.1D Spanning Tree Protocol?
A: Ports listen and learn before going into the forwarding state.
Q: Which industry-wide specification was developed to decrease the time that is needed to move to the forwarding state by switch ports that are operating in a redundantly switched topology?
A: RSTP
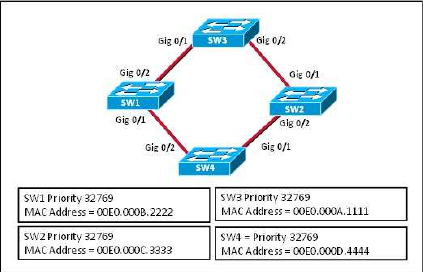
Q: Refer to the exhibit. Which switch will be elected the root bridge and which switch will place a port in blocking mode?
A: SW4 will get a port blocked.
A: SW3 will become the root bridge.
Q: A router with two LAN interfaces, two WAN interfaces, and one configured loopback interface is operating with OSPF as its routing protocol. What does the router OSPF process use to assign the router ID?
A: The loopback interface IP address
Q: What table does the EIGRP DUAL algorithm use to calculate the best route to each destination router?
A: Topology table
Q: What two measures are used to prevent routing loops in networks that use distance vector routing protocols?
A: split horizon
A: hold-down timers
Q: What best describes the operation of distance vector routing protocols?
A: They send their routing tables to directly connected neighbors.
Q: A router needs to be configured to route within OSPF area 0. Which two commands are required to accomplish this?
A: RouterA(config)# router ospf 1
A: RouterA(config-router)# network 192.168.2.0 0.0.0.255 area 0
Q: What guideline is generally followed about the placement of extended access control lists?
A: They should be placed as close as possible to the source of the traffic to be denied.
Q: Which two pieces of information are required when creating a standard access control list?
A: source address and wildcard mask
A: access list number between 1 and 99
Q: Which two keywords can be used in an access control list to replace a wildcard mask or address and wildcard mask pair?
A: host
A: any
Q: What are three Frame Relay congestion management mechanisms? (Choose three.)
A: BECN
A: DE
A: FECN
Q: What is the default Layer 2 encapsulation protocol for a synchronous serial interface on a Cisco router?
A: HDLC
Q: Which network device is commonly used to allow multiple VPN connections into a corporate network?
A: Concentrator
All these and other questions as PDF:

Leave a Reply