This is my second OpenVPN road warrior setup, I write this post from my first pre created drafts. Its more than one year ago, I combined some steps and command, to make it human readable and a little bit friendly :)
First we need to install the needed OpenVPN package:
1 | apt-get update && apt-get install openvpn |
Copy the helper scripts to make the life easier, they will help you to create keys and certificates:
1 | cd /etc/openvpn ; mkdir easy-rsa ; cp /usr/share/easy-rsa/* easy-rsa/ ; cd easy-rsa |
Fix the default values:
1 2 3 4 5 6 | vim vars export KEY_COUNTRY="DE" export KEY_PROVINCE="Niedersachsen" export KEY_CITY="Hannover" export KEY_ORG="Debianuser" export KEY_EMAIL="vpn@debianuser.org" |
Source the variables
Set up the keys environment
Build the certificate authority
Build the certificate and private key for the server
Build the client certificate for your first user/client
Build the Diffie Hellman
1 | . vars ; . clean-all ; . build-ca ; . build-key-server server ; . build-key-pass YOURUSERNAME ; . build-dh |
After execution, your certificate will be generated. The most steps/questions we have already hard coded in our vars file, that men they can be answered with RETURN.
Verify that you choose a secure passwords.
Create server side configuration:
1 | vim /etc/openvpn/server.conf |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 | # Which local IP address should OpenVPN # listen on? (optional) # local a.b.c.d # Port port 1194 # Protocol TCP|UDP proto udp dev tun # Certificates ca ca.crt cert server.crt key server.key dh dh1024.pem # Configure server mode and supply a VPN subnet server 10.8.0.0 255.255.255.0 # Maintain a record of client <-> virtual IP address # associations in this file. ifconfig-pool-persist ipp.txt # Push routes to the client to allow it # to reach other private subnets behind # the server. push "route 192.168.2.0 255.255.255.0" # To assign specific IP addresses to specific # clients client-config-dir ccd push "dhcp-option DNS 8.8.8.8" # The keepalive directive causes ping-like # messages to be sent back and forth over # the link so that each side knows when # the other side has gone down. # Ping every 10 seconds, assume that remote # peer is down if no ping received during # a 120 second time period. keepalive 10 120 comp-lzo # The persist options will try to avoid # accessing certain resources on restart # that may no longer be accessible because # of the privilege downgrade. persist-key persist-tun # Output a short status file showing # current connections, truncated # and rewritten every minute. status openvpn-status.log # Set the appropriate level of log # file verbosity. # # 0 is silent, except for fatal errors # 4 is reasonable for general usage # 5 and 6 can help to debug connection problems # 9 is extremely verbose verb 4 |
Create client default configuration:
1 | vim client.ovpn |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 | # OpenVPN configfile # Client-modus client # Interface dev tun nobind # Server remote kvm.debianuser.org 1194 proto udp resolv-retry 15 # Compression comp-lzo # Try to preserve some state across restarts. persist-key persist-tun # Certificates ca ca.crt cert username.crt key username.key # Security section auth-nocache remote-cert-tls server script-security 2 ns-cert-type server # Set log file verbosity. verb 6 |
Create client configs for your first user:
1 | mkdir zeldor.config ; cp client.ovpn zeldor.config/zeldor.ovpn ; sed -i "s,username,zeldor," zeldor.config/zeldor.ovpn |
Copy client certificates:
1 | cd easy-rsa/keys ; cp ca.crt zeldor.crt zeldor.key ../../zeldor.config/ |
Create symlinks for server certificates:
1 | cd /etc/openvpn ; ln -s easy-rsa/keys/ca.crt ; ln -s easy-rsa/keys/ca.key ; ln -s easy-rsa/keys/dh1024.pem ; ln -s easy-rsa/keys/server.crt ; ln -s easy-rsa/keys/server.key |
To connect to your OpenVPN server install a Client and copy all files from user.config to the client PC.
In my case, I use Nokia N900 to establish connection with OpenVPN-Server:
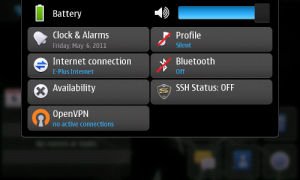
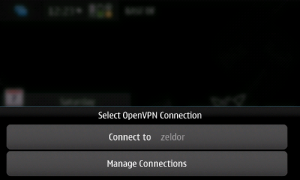
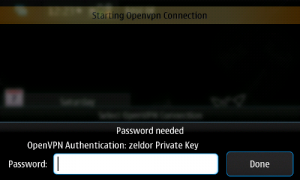
Create another new user:
1 | cd /etc/openvpn/easy-rsa/ && . build-key-pass USERNAME2 |
A specific user should get a static IP-Address:
1 2 3 4 5 6 | mkdir /etc/openvpn/ccd vim /etc/openvpn/ccd/zeldor # content of file zeldor # Static IP ifconfig-push 10.8.0.37 10.8.0.38 # user zeldor will get IP 10.8.0.37 |
All traffic goes in the tunnel:
1 2 | cat /etc/openvpn/ccd/zeldor push "redirect-gateway def1 bypass-dhcp" |


Leave a Reply