SSH-tunnels are very useful to access server or PCs behind firewall. Normally these components are behind NAT and have only a LAN-IP. To access them you will need to create a DNAT rule but this possibility is not secure like SSH protocol.
To create a ssh tunnel you need only a running ssh-server on the firewall of your destination site.
Example one:
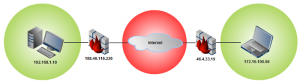
Create ssh tunnel to access the RDP Port on LAN-PC 192.168.1.10
From laptop(172.16.100.56) issue this command to create a ssh tunnel to your home PC:
1 | ssh -N -L 4652:192.168.1.10:3389 root@188.40.116.226 |
After you type in your password you will be able to connect to RDP: localhost:4652
OR this method:
1 | ssh -N -L 172.16.100.56:80:192.168.1.10:80 root@188.40.116.226 |
After you type in your password you will be able to connect to HTTP: http://172.16.100.56/
Example two:
Create a reverse ssh tunnel from laptop(172.16.100.56) to your home firewall. This will allow you, to access the ssh port of your laptop from your firewall.
1 | ssh -NXC -R 42005:localhost:22 root@188.40.116.226 |
From the firewall at home you will be able to access your laptop ssh port:
1 | ssh -p 42005 username@localhost |
Extended example two:
This is only a extended example two, with this reverse tunnel you will be able to access your laptop ssh port from everywhere.
1 | ssh -NXC -R 188.40.116.226:42005:localhost:22 root@188.40.116.226 |
Access the port 22 on your laptop at work:
1 | ssh -p 42005 username@188.40.116.226 |
Enable GatewayPorts yes in yoursshd_config to use ssh tunneling.
Conclusion:
– you don’t need a VPN between two LANS
– unsecure protocols can be simple run over secure shell
– firewall worm


Leave a Reply